Robert Rozario
Infineon Technologies North America Corp.
The counterfeiting and cloning of devices and peripherals are major concerns for original equipment manufacturers (OEMs). These concerns grow when manufacturing is outsourced to offshore Contract Manufacturers (CMs) or even to multiple CMs, which can make it almost impossible to protect the intellectual property (IP) and prevent the unauthorized production of gray market products and peripherals. Legitimate suppliers not only suffer direct revenue losses, but also lose brand reputation if a product is damaged as the result of using cloned peripherals, and may even incur high liability costs.
Another problem OEMs face is that many new products are subsidized when introduced to the market, with the intent of profiting on sustained after-market sale of accessories and add-ons to recover the initial investment. This business model is often followed with such products as accessories for game consoles, mobile devices and printer cartridges. Cloning poses a serious threat to this business model; unauthorized accessories can even create a hazard risk to the end-users that increase the potential liability costs and damage OEMs’ brand reputation. Tamper- and counterfeit-resistant peripherals not only protect OEMs’ brand image and liability, but also protect consumers by assuring the integrity of the entire system and creating the intended user experience.
Why Authentication?
There are many classes of after-market parts and accessories that are built to be compatible with OEM specifications and standards (notebook AC adapters and batteries). Often there are both legitimate accessories manufactured by authorized third parties, and unauthorized counterfeit/clone devices that appear to be legitimate products but may not meet the operating or safety specifications of the OEMs. Authentication deals with how the system identify authorized parts from unauthorized ones. Authentication of accessories covers all aspects of brand protection such as safety, reliability, quality, profit, performance and liability. It is increasingly important in light of current technology trends, such as high-energy density batteries, different voltage levels in the same form-factor batteries, fast charging and the ability of one single adapter to charge multiple types of mobile devices.
Why Hardware Authentication?
There are many tactics available to manufacturers to address anti-cloning issues. While in many cases some degree of success is achieved, it is often short lived. Patents, custom connectors and proprietary hardware/software solutions are used to thwart attackers, cloners and hackers with variable success rates. It is always a challenge to make both the platform and its accessories tamper-resistant. A relatively new approach is the use of embedded authentication hardware to ensure an accessory or peripheral is authorized for use with a given system. This can provide a high degree of security for counterfeit prevention compared to the alternatives. With different approaches available to the OEMs, it is important to understand the underlying technology to choose the right authentication solution for a certain application.
How Authentication Works
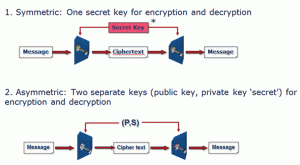
An important consideration in counterfeit protection is the cryptographic system that is used. There are two main types of cryptographic algorithm used in hardware authentication solutions, as shown in Figure 1.
In consumer electronics and computers, the symmetric solution (in which the host and peripheral share the same secret) may fall short if the shared secret is exposed and counterfeit devices can be made that are guaranteed to work with all host systems.
Asymmetric cryptography uses two different keys for encryption and decryption. The “public key” can be made public (used in the software that resides in the host system). The other secret, “private key”, remains hidden in the safe environment of a chip embedded in the peripheral. The public key information cannot be used to derive the secret key information, so it does not need to be protected (using hardware or software) as rigorously as the symmetric key solution. Figure 2 shows an illustration of how asymmetric authentication works.
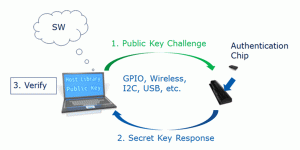
Asymmetric authentication works as follows. When a peripheral is detected (attached to the system), the host uses the public key and another parameter (such as a random number) to generate a challenge and send it to the hardware authentication chip residing in a peripheral. The authentication chip uses the challenge and its secret key to generate a response and transmit it to the host. The host verifies the response and upon successful verification, allows the peripheral to function properly. If the verification fails, it is up to the host side to decide which type of action to take. It could warn the user about the unauthorized device, stop charging or prevent the peripheral from being used with the system. The communication interface between the host and peripheral depends on the type of peripheral and architecture of the system.
What are the Challenges in Preventing Counterfeiting?
The success of hardware authentication relies on both chip technology and business decision made by the OEMs. The challenges to be considered include the following:
1. Security is a moving target: there is no absolute security in any solution. What is completely secure today (be it the hardware or cryptographic algorithm) may not be secure after a period of time due to advancements in technology and tools that are used to circumvent the authentication scheme.
2. Attacks always happen on the weakest link in the security chain. Both the hardware authentication device and the entire security chain must be secure, beginning with manufacturing of the authentication chip, key injection process, transportation of the chips to the manufacturing site, accessory manufacturing and the security programs the end-users will uses.
3. Nothing is unbreakable. Provided with the right resources and tools any security can be overcome, it is a question of how long it takes to break and what resources someone is willing to invest.
4. While high-end security controllers provide a higher degree of protection and additional security features, cost plays a role in choosing the right authentication solution for a particular application. Any potential solution must carefully balance production cost and efforts against the level of difficulty of cloning the peripherals.
What are the Selection Criteria for an Ideal Authentication Solution?
A successful anti-counterfeiting solution must answer the following seven questions:
Is the host system immune to attacks?
There are different types of host-side software implementation. If the code is implemented in a controller firmware or in BIOS (pre-boot phase), the attacks could come from someone who has physical access to the system. If the code is implemented in a Post OS phase, then the attacks could come from remote entities. Attacks to host systems are aimed at retrieving the secret, which would allow counterfeiters to build clones. In the case of asymmetric solutions, host code and libraries only contain public information; the attacker cannot gain any knowledge of the private secret held within the authentication hardware protected boundary. An attack on the host, in order to find the secret key to enable cloning, is therefore futile. From this perspective, the Host system is immune to attacks.
Is the peripheral immune to attacks?
Unless anti-cloning solutions incorporate some level of protection, reverse engineering would reveal the secret recipe necessary for cloning. The hardware authentication chip should incorporate physical security to protect its secret. By using an asymmetric protocol, attacks via bus snooping (monitoring electrical signals on the chip) will not reveal any secrets. The chip implementation should also include protection against replay, side-channel and power analysis attacks. This type of hardware protected solution is relatively immune to attacks, especially when it comes to large scale commercial cloning.
Is the key injection process secure?
Secret Key injection in the hardware authentication chip is one of the weakest links in the security chain. The secret key can be retrieved by an insider or it can be retrieved by an outsider during the key injection process. Thus, the key injection process needs to take place in a secure manufacturing site, preferably when the chips are still at the wafer level, utilizing isolated and secure network connections so that the secret key is never exposed outside the network. A Common Criteria certified manufacturing facility is preferred for the key injection process as the facility is audited for various security measures.
Is the security infrastructure programmable with after-market parts?
If the security parts are available as blanks (no secret key) and they can be programmed with the secret key at packaged level, then a counterfeiter will try to get the secret key and the authentication scheme can be compromised. Hence, no blank packaged parts should be available for anyone to purchase or obtain by any means. Packaged parts also need to be locked so that the secret key can never be reprogrammed.
How can one prevent the reuse of expired parts/accessories?
The recycled battery business is thriving for various reasons such as:
• Counterfeiters do not need to invest in plastic molding of batteries or on electronic components like fuel gauge, protection IC, authentication and PCB.
• Repackaging batteries with cheaper inferior cells allows the battery to appear as a genuine OEMs brand product.
• These batteries pass authentication verification without any investment in reverse engineering of authentication part or process.
To prevent this type of recycling, the authentication hardware should have some mechanism for lifecycle management. For example, an irreversible life span counter that keeps track of charging/discharging cycles and a memory space where some battery cell characteristic can be safely stored can be used to detect the change of the cells in a recycled battery.
Is there a chance to break a single device and use the information to hack all the systems?
In a symmetric solution where all the authentication hardware parts have the same secret key, counterfeiters might be tempted to break one to get the secret key and clone the authentication process. It is advisable for each individual customer to have a unique public-private key pair, which allows the OEMs to monitor part consumption to ensure that there is no over production for the gray market and discourages counterfeiter attempts to break the solution. For further enhancement of security, each chip can have its own public-private key pair and the public key can be placed in a signed digital certificate inside the authentication chip. In this case, the host first verifies the certificate and then uses the public key for authentication.
Is it cost effective and easy to implement?
Although many security controllers will meet all the criteria mentioned above, they also cost more. There is a fine balance between cost, degree of security and ease of implementation. The authentication chip needs to be architected and designed with all these factors in mind; it can meet stringent security requirements while allowing easy implementation with reasonable cost structure. Authentication chip manufacturers should provide the complete host code library package, which simplifies the implementation process and saves time. The key personalization process at chip manufacturing site also relieves the OEMs and CMs of key management logistics, key injection steps and secret leakage issues, which helps from a cost and implementation perspective.
Conclusion
It is a well understood fact that certain applications require an efficient level of security while being cost sensitive. For example, printer cartridge manufacturers would like to protect their revenue stream, and cell phone manufacturers would like to protect their device reliability and brand via anti-cloning techniques. However, both applications are cost sensitive in nature. Manufacturers should identify a hardware authentication chip that addresses the requirements for peripheral authentication and is an economically justifiable and easy to implement solution.
For more information, please contact Infineon Technologies North America at
ORIGA@infineon.com or www.infineon.com/ORIGA.







